¶ RDP Comes in Flavours
There are different scenarios when in comes to RDP logins. You can have SSL negotiation switched on or off, your client can be within your organizational network or outside, NLA can be switched on or off, you can even have SSO enabled or use an RDP web access portal. Depending on the scenario, your experience will vary, and SystoLOCK does not support all of them.
It is important to mention that SystoLOCK is, in its core, a smartcard subsystem, and RDP handles smartcards in a very special fashion, not like other devices, connected to your client. This fact places some restrictions on what to expect from SystoLOCK in each scenario. In most cases that also means that you need to have SystoLOCK Client installed on both your workstation and the target RDP server(s).
¶ A Regular RDP From Inside Your Network
This scenario is no different from impersonation: just key in your credentials triplet (user name, PIN, OTP) and, if your RDP server is configured normally, you are in.
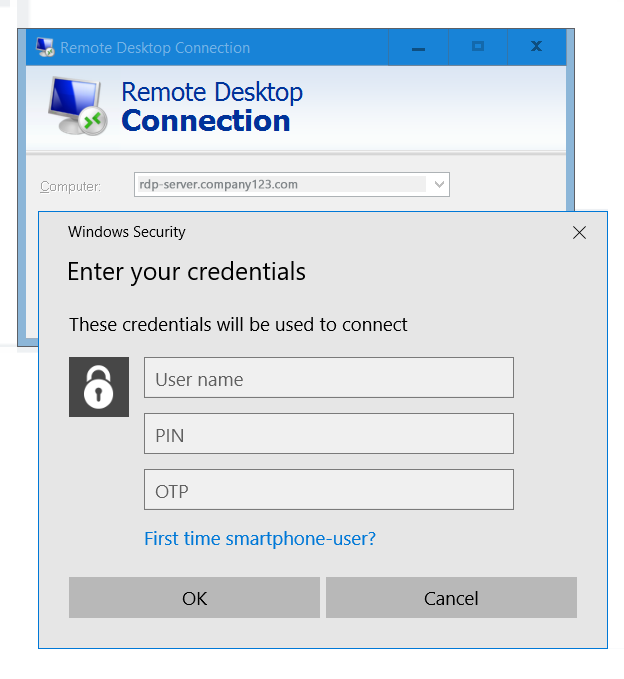
¶ Connecting from Outside
If you are connecting from outside, you can either connect directly as from inside or you can take advantage of RDP gateway feature of your farm and configure to use your credentials for both, the gateway and the target RDP server.
SystoLOCK does not support RDP web access SSO directly, meaning that you will have to provide your credentials again upon web-app start.
¶ RDP with RC4 (RDP security) on
If your RDP server is configured not to negotiate SSL and uses old encryption scheme, you will be presented with a login screen, just like with a regular login, where you enter your new credentials.
¶ Nested RDP Sessions
SystoLOCK generally supports nested RDP, for that scenario to work you need to make sure all members in the RDP chain have SystoLOCK Client installed. In certain cases you might experience a second prompt for credentials, as if the setting "Always prompt for credentials" were on.
¶ Impersonation Inside RDP
If you have an RDP server with RC4 encryption and need to use impersonation or similar scenarios, you would need to tweak you Client installation on the server by setting "Use KSP in CredUI" on. See Client Post-installation Tasks and Managing Client Settings with GPO for more detail.