¶ Configure AD FS federation
It is good practice to follow the Entra ID Security Defaults, and for some users you will not even be able to turn them off. In addition, Microsoft has enforced MFA for certain accounts accessing Entra ID as of October 2024.
If you are federating SystoLOCK with Entra ID via AD FS, there are a few steps required for Entra ID to recognise your federation as MFA based. You will need to configure both your AD FS setup and your federation setup.
¶ Configure AD FS
This step may have already been done by another tool such as Entra ID Connect. Check that the entry described below is present.
Open your AD FS management console and navigate to 'Relying Party Trusts'. Find your Microsoft 365 registration there, it will look similar to this:
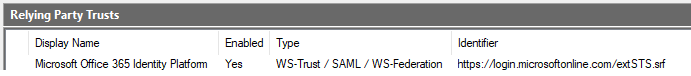
Select it open Edit claim issuance policy... in the task pane on the right. Click on Add Rule, select 'Pass Through or Filter an incoming claim', click Next, name the new rule and select Authentication Methods References as incoming claim type, click Finish to save the rule and OK to save the rule set.
¶ Configure the Tenant
Open the PowerShell console and execute the following commands, replacing <domain> with the domain name of your federation:
# 1. Install the required Graph module (only needs to be done once)
Install-Module Microsoft.Graph.Identity.DirectoryManagement
# 2. Connect to Microsoft Graph with the required permission scope
Connect-MgGraph -Scopes "Domain.ReadWrite.All"
# 3. Update the domain federation settings
Update-MgDomainFederationConfiguration -DomainId "<domain>" -SupportsMfa $true -PromptLoginBehavior "nativeSupport"
# 4. Verify the settings
Get-MgDomainFederationConfiguration -DomainId "<domain>" | Select-Object PromptLoginBehavior, SupportsMfa
# Output:
# PromptLoginBehavior SupportsMfa
# ------------------- -----------
# NativeSupport True
Legacy method:
Import-Module MSOnline
Connect-MsolService
Set-MsolDomainFederationSettings -DomainName <domain> -PromptLoginBehavior NativeSupport -SupportsMFA $true
Get-MsolDomainFederationSettings -DomainName <domain> | ft PromptLoginBehavior,SupportsMfa
This will tell the tenant that your AD FS is capable of handling MFA authentication natively, so Entra ID will send the appropriate claim with the request, while the claim policy described above will ensure that this authentication type is returned to the requestor.