¶ Follow these steps if you need to completely remove SystoLOCK from your environment. Make sure to follow the order of the steps outlined below.
Make sure you configure passwords for your users prior to uninstalling SystoLOCK, so that they are able to login into their accounts.
Make sure you have sufficient privileges before running the scripts below.
¶ 1. Uninstall the binaries
- Uninstall the clients either from the Control Panel or via group policy or other software management system
- Uninstall AD FS Adapter(s), the server(s) and management tools via Control Panel
- Deregister any RDS Gateway and RDWeb plugins with corresponding PowerShell scripts and uninstall those components via Control Panel
¶ 2. Remove AD CS Templates
Certificate templates can be removed from the CA configuration with no harm. You can remove them manually of via PowerShell.
This script removes the template information from the domain:
$Domain = Get-ADDomain
$Path = "ad:\CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,$Domain"
ls $Path | ? name -like 'SystoLOCK*' | Remove-ADObject
This script removes the template assignments from the individual CA server(s):
$Domain = Get-ADDomain
$Path = "ad:\CN=Enrollment Services,CN=Public Key Services,CN=Services,CN=Configuration,$Domain"
ls $Path -properties certificateTemplates | % `
{
$CA = $_
$CA.certificateTemplates | % `
{
if ($_ -like 'SystoLOCK*')
{
Set-ADObject $CA -Remove @{certificateTemplates=$_}
}
}
}
¶ 3. Remove Rights Assignments
Using any Active Directory browser (i.e. AD Users and Computers), set the rights to the root of the domain by removing any ACEs that refer to 'SystoLOCK Services':
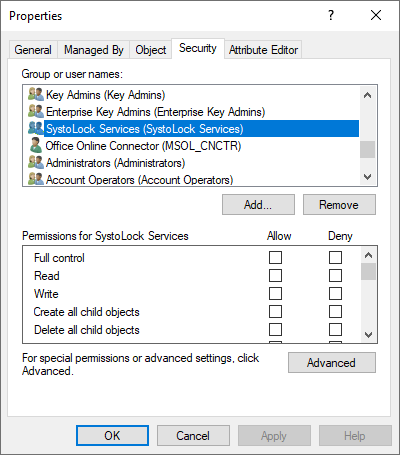
Using the following PoweShell script, check if there are any rights assignments with broken inheritance or any admin users with special security descriptors. Adjust the rights for the objects found manually.
$Domain = Get-ADDomain
$DomainNBName = $Domain.NetbiosName
$SystoLOCKGroup = "$DomainNBName\Systolock Services"
$Filter = '(|(objectclass=container)(objectclass=organizationalUnit))'
ls "ad:\$Domain" -Recurse `
-Filter $Filter `
-Properties canonicalName,ntSecurityDescriptor | % `
{
$OU = $_
if ($OU.nTSecurityDescriptor.Access.IdentityReference -contains $SystoLOCKGroup)
{
Write-output "Container: $($OU.CanonicalName.Substring($OU.CanonicalName.IndexOf('/')))"
Get-ADUser -Filter '*' `
-SearchBase $OU.distinguishedName `
-SearchScope OneLevel `
-Properties adminCount,canonicalName,ntSecurityDescriptor | % `
{
$User = $_
if ($User.nTSecurityDescriptor.Access.identityreference -contains $SystoLOCKGroup)
{
if ($User.adminCount)
{
Write-output "Admin: $($User.CanonicalName.Substring($User.CanonicalName.IndexOf('/')))"
}
else
{
Write-output "User: $($USer.CanonicalName.Substring($User.CanonicalName.IndexOf('/')))"
}
}
}
}
}
If the script finds any 'admin' objects, you would also need to adjust the rights assignments on the System/AdminSDHolder object under the root of your domain. The rights assignments for the admin users will then be applied automatically.
¶ 4. Remove Group Policy Objects
SystoLOCK creates a couple of GPOs that you no longer need, so the following script will delete them. If you have created GPOs with similar names that you do not wish to remove, adjust the script accordingly.
Get-GPO -all | ? DisplayName -like SystoLOCK* | Remove-GPO
¶ 5. Remove SystoLOCK Container
Finally you can remove the AD container that holds SystoLOCK data using a tool of your choice or via the following PowerShell script:
$Domain = Get-ADDomain
$Path = "CN=Systola,CN=Program Data,$Domain"
Get-ADObject -LDAPFilter 'objectClass=container' -SearchBase $Path | `
Set-ADObject -ProtectedFromAccidentalDeletion $false
rm "ad:\$Path" -Recurse -Force
¶ 6. Remove AD CS
If you installed an AD CS role only to be used with SystoLOCK and do not plan to use it any further, you may wish to uninstall this component, too.
Follow this guide from Microsoft to decommission a Windows enterprise certification authority and remove all related objects from Active Directory.