¶ A Glance From Above
SystoLOCK changes several aspects of the whole authentication mechanisms in Windows:
- Redefines user credentials from a doublett of username / password to a triplett of username / PIN / OTP (One-Time-Password).
- Disables password authentication for selected users.
- Adds a new type of credential provider that collects new credentials upon login requests.
- Translates new credentials into PKI-bound elements acceptable by domain controllers.
- Creates an infrastructure that provides for managing of the new aspects: credentials, tokens and settings.
¶ System Components
SystoLOCK is a distributed system and consists of several components, that rely on each other as well as on some basic components of Active Directory.
¶ SystoLOCK Authentication Server
In the heart of SystoLOCK lies SystoLOCK Server, a lightweight service that is central to the installation, it processes the complete business logic of all processes that take place within SystoLOCK infrastructure. There could be (and, normally, there are) several SystoLOCK Server within one domain to ensure reliability and redundancy. Usually one SystoLOCK instance is installed for each domain controller.
¶ SystoLOCK Client
Also called Windows Client, it is a driver that is plugged into standard Windows authentication mechanics. It allows for collection of the new SystoLOCK credentials is responsible for sending these credentials to SystoLOCK Server.
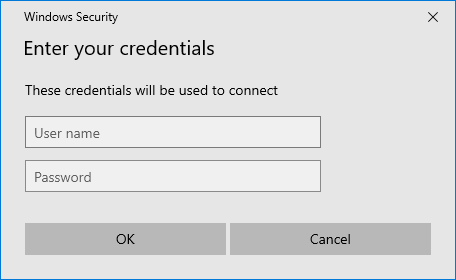
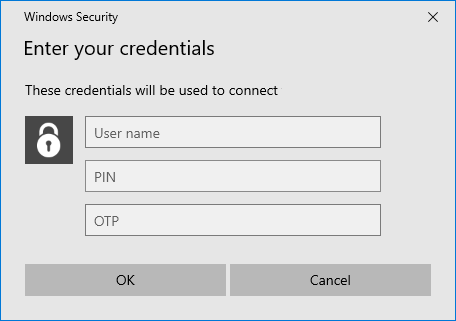
Windows Client changes the way all authentication dialogs are presented to the user:
| Standard Windows Prompt | SystoLOCK Prompt | |
|---|---|---|
 |
 |
Windows Client is also responsible for managing dial-up connections for VPN, for setting some advanced client options and for collecting diagnostic information, should a need for troubleshooting arise.
¶ Domain Controllers
Domain controllers are not technically part of SystoLOCK infrastructure, but SystoLOCK relies on them and cannot work without a domain infrastructure. SystoLOCK cannot be used to provide MFA for workgroup scenarios.
¶ Certification Authority
A domain can function without a CA, but SystoLOCK requires an enterprise mode CA to be installed and constantly available for user certificates to be issued, since each authentication attempt results in a new, short-lived, user certificate to be issued from that CA.
Server Installer will fail if it does not find a valid CA installed.
¶ DNS servers
When a Windows Client performs an authentication attempt, it first tries to discover a SystoLOCK Server it will talk to. This discovery relies on DNS to be configured properly. This configuration is done by an the Server installer, is Microsoft DNS is used or it can also be tweaked manually in other cases.
¶ AD FS Adapter and Identity Provider
For scenarios where you need to access a web-based resource, such as Outlook Web App (OWA) or Office 365, where users are prompted with a form-based authentication pages, SystoLOCK relies on AD FS infrastructure to take over and perform authentication.
An AD FS Adapter or Identity Provider are provided to to be installed on AD FS servers and act as Clients for SystoLOCK Server and will process the needed credentials:
¶ SystoLOCK Companion
SystoLOCK Companion is a mobile application that is used to generate OTPs and can hold many accounts, similar to many OTP-generating apps, such as Google Authenticator. Most important role the Companion plays in s.c. Assisted Login - a number of login scenarios, where the credentials are submitted partially or completely over the phone's mobile connection, thus making it easier and more secure.
¶ Authentication Flow
Contrary to a regular authentication, where a client speaks directly to a domain controller, SystoLOCK authentication works a little different.
The diagram below summarizes the authentication flow with SystoLOCK:
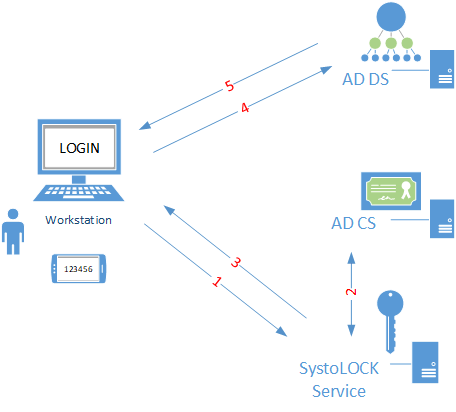
- Credentials (user name, PIN and one-time-password) are sent to SystoLOCK server for validation.
- Upon successful validation, SystoLOCK server obtains a Certificate from a certification authority and ...
- ... returns the certificate to the client.
- The client then presents the certificate to a domain controller.
- The domain controller authenticates the client.